RCMP unit plays cat-and-mouse game to crack phones, seize data
They can find out who you've talked to, where you've been and what sites you've browsed on the internet.
Deleting information or smashing a computer hard drive isn't going to thwart their efforts either.
They are the members of the RCMP Technological Crime Unit.
From a nondescript series of rooms inside Nova Scotia's RCMP headquarters in the Burnside Industrial Park, the unit provides technical support to police and government agencies across the province and beyond.
"It's a game you play," said Sgt. Royce MacRae, who heads the unit.
"The industry creates new ways to stop the data from being brought out. We'll come up with new methods, new techniques to recover that data."
MacRae said sometimes police efforts to extract data are thwarted by encryption technology.
He said in those cases, his team may set the phone or other device aside and come back at it weeks or months later. That's how quickly the technology in this cat-and-mouse game can evolve.
Time-consuming work can take months
The search for data is tempered and restrained by the need to protect privacy and work within the confines of the law, he said.
"The days of just giving everything on the phone, that's not the way it works any more," he said.
"Investigators are asking for the stuff and they've explained to a judge why they need that, and that's what we provide."
It can be finicky, time-consuming work. MacRae chafes a bit at the unrealistic expectations created by TV crime shows where all cases are solved in 45 minutes, plus commercials.
"An average phone, if it's not encrypted, if it's not using anything, usually within half a day we can have the phone done and a report out to the investigator," MacRae said.
But he said extracting data can also take days or even weeks.
Special equipment developed
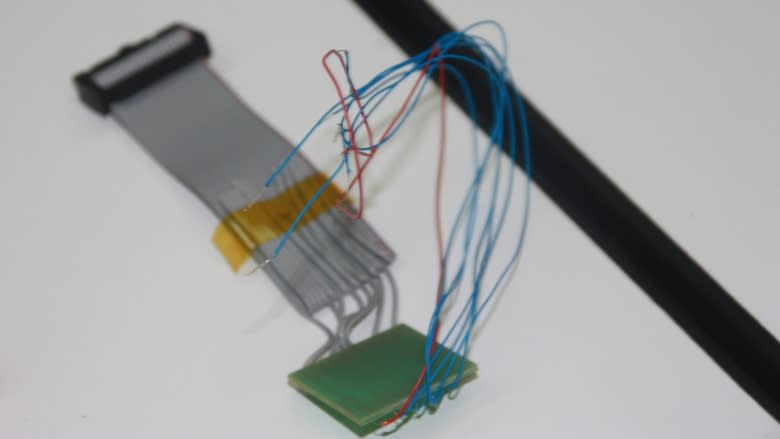
MacRae points to a tiny, fragile device consisting of 10 monofilament wires and a plug. Experts in his unit can carefully solder those 10 wires directly onto the motherboard of a phone.
The plug on the other end of the device then goes directly into a police computer, allowing officers to start accessing the contents of the phone. He said those seized phones can provide a wealth of information on criminal activity.
"You're going to have location data, text messaging, voice call records," MacRae said.
"Everything you can think of you use your phone for — if our investigators can find a reason that they need that for the court process, they'll write a warrant for that and we'll recover that data for them."
GPS devices can be useful
MacRae said it isn't just about tracking criminals. The location data stored on phones can also help locate people who've gotten lost.
GPS devices used in cars to tell us where we're going can also provide information to police on where we've been. That's particularly useful for investigators trying to track the movements of drug dealers or other criminals whose movements are key to their crimes.
"If you printed off every piece of data on that hard drive from start to finish, you'd have a stack of paper 2 1/2 times the height of the CN Tower," Bembridge said.
Random searches could take forever
With today's computers holding terabytes of data, it's not feasible to go on random searches. He said the experts will instead use keyword searches and other techniques to try to zero in on the specific data investigators need.
That data can include images, especially when investigators are working on child exploitation and child pornography cases. Bembridge has a warning for people who post intimate images online.
"You can put it online, the offender may send that information on to his or her friends and people may be arrested for it," he said.
"They may be convicted, they may go to jail for that offence. But the pictures are still out there. And it's not coming back."
Bembridge said pictures, like all online files, carry their own unique electronic fingerprints. He said some child porn images that are shared again and again can be identified by police simply by searching for the distinct fingerprint attached to each image.
Electronic fingerprints in images
While most of their data searches focus on cellphones and computers, the tech crime experts can also extract useful information from a variety of devices.
MacRae said the information his unit extracts and the techniques they use are not readily available to everyone.
He said with the constantly evolving state of technology, it is a costly, time-consuming effort to stay on top of these types of crimes and the devices that are involved.