5 big questions about cyberattacks during COVID-19

The hospital in Kemptville. The transit network in Gatineau. The municipal government in Clarence-Rockland.
Those are just a few of the Ottawa-area organizations victimized in recent weeks by cybercriminals, emboldened as the COVID-19 pandemic forces people to work from home and more and more business gets conducted online.
The health-care sector in particular has proven a juicy target: just this month, the Rideau Valley Health Centre also experienced a "cybersecurity incident" that took down its IT network.
And it's not just happening locally, with criminals carrying out a devastating attack on Newfoundland and Labrador's health-care network, stealing personal information connected to both employees and patients.
So how bad is the situation? Why is the pandemic exacerbating things? And what can organizations do to protect themselves? We put those sorts of questions to a pair of experts in the cybersecurity field, and here's what they had to say.
What kind of attacks are organizations facing?
Two of the most common attacks are phishing scams and the surreptitious installation of ransomware, according to Det. Sgt. Vern Crowley with the Ontario Provincial Police's Cybercrime Investigation Team.
Phishing attacks generally involve someone, somewhere, trying to lure people into providing personal information like passwords or banking information.
Just this week, an Ottawa man was one of three people arrested in connection with an alleged phishing scam that breached the province's COVID-19 immunization system.
Ransomware, on the other hand, is malicious software that — once it's been installed — encrypts data, forcing users to pay a ransom, usually in the hundreds of thousands of dollars, in exchange for the tools to regain access.

Have they really become more common during the pandemic?
The broad consensus appears to be that yes, the COVID-19 pandemic is contributing to a rise in cybercrime.
The Canadian Centre for Cyber Security (CCCS) has said crimes are being reported more frequently, especially lucrative ransomware attacks on the country's front-line health-care and medical research facilities.
Federal government employees working from home on virtual private networks (VPNs) were also warned in the early days of the pandemic to be on alert for phishing attacks.
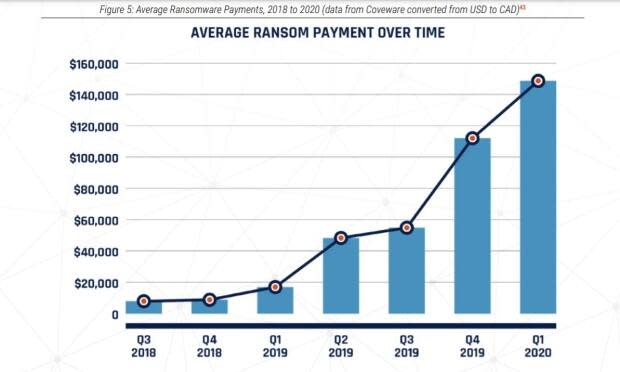
Crowley said his team has "absolutely" seen attacks climb during COVID-19, as many organizations pay ransoms to get their data back and cybercriminals realize they can make a quick buck.
"A lot of criminals are just moving to the online world," he said. "It's been going on across the board. Every sector we see getting hit."
Why is health care such an appealing target?
According to iSecurity Consulting's Raheel Qureshi, whose firm works with dozens of Canadian hospitals and other health-care organizations, there are two big reasons.
The sector's highly integrated nature, with hospitals and clinics sharing patient records and exam results back and forth, means criminals can exploit weaknesses and encrypt data without anyone noticing, Qureshi said.
"The more complex your ecosystem is, the more difficult it is for you to detect and manage and track, right? Not that it can't be done, [but] there's a lot of investments required," he said.
"They're not in the business of cybersecurity. They're in the business of providing patient care."
What's more, when IT networks in the health-care field go offline, it can put people's lives at risk — and ransomware attackers know that urgency gives them leverage.
"The health-care sector is paying when it needs to," Qureshi said. "It's been a very lucrative business for these threat actors."
So how can organizations stay safe?
The best thing many organizations can do, Qureshi says, is to get a firm like his to perform a simulated ransomware attack: a two-to-three-week exercise that will pinpoint their IT weaknesses and offer solutions to fix them.
Individuals should also be tested, perhaps with a fake phishing attack, so that they know how to spot signs of danger and respond correctly, he adds.
Crawley says it's a good idea for organizations to ensure all important data is backed up offline. Those that use VPNs should implement multi-factor authentication to gain access — a password combined with, say, a one-time code sent via text message.
He says it's also important to keep on top of the latest cybercrime hacks and trends, whether that's through monitoring CCCS's alerts and advisories or checking for malicious websites through the non-profit Canadian Internet Registration Authority.
Ultimately, groups should always have a playbook to both prevent attacks and react if there's been a breach, Crawley said — one that involves notifying police. Different police forces can then cooperate on investigations to track down the perpetrators across the country and around the world.

If they're hit with ransomware, should they pay up?
It's a complicated question, and there's no easy answer.
Many perpetrators are "very professional in an unethical way," Qureshi says. Organizations that submit to the ransom demands generally get complete instructions for decrypting their files, around-the-clock service, and sometimes even text files explaining how to shore up their online defences.
Qureshi's theory is that "brilliant" hackers in developing countries may turn to cybercrime only because they lack the legitimate opportunities in places like North America or Europe, and don't bear any ill will to their targets.
"Deep down inside, they feel bad it's a hospital. But they don't feel bad, because at the end of the day, they think of it as a professional transaction," he said. "It's a different world."
Still, police would never condone paying a ransom, Crawley says — after all, you can't trust criminals to do what they say they'll do, and it just encourages them to keep breaking the law. But he also understands why someone might decide it's best to just cough up the money to make the problem go away.
"If you're in that level of jeopardy and have to do it, that's a business decision," Crawley said.
"All we say [from the] law enforcement side is, please ensure that you preserve any digital evidence in relation to the financial transactions or communications, so that we can get these guys."


