Qulliq Energy stops short of labelling cyberattack another Nunavut ransomware incident

The Qulliq Energy Corp. says it was locked out of its data in January's cyberattack, but stopped short of calling it a ransomware attack.
QEC announced last month it fell victim to a cyberattack, which was discovered on Jan. 15. While no operating technology, such as power plant infrastructure, was affected, QEC's information technology, like email, billing and payroll databases were.
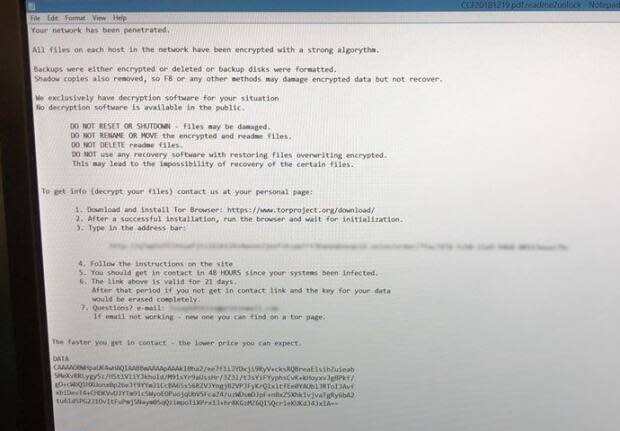
"There's different levels of cyberattacks," said Bill Nippard, QEC's vice-president of operations and engineering. "In some cases they steal your data. In other cases, they simply lock your data out and encrypt it. So, at this point, we're still continuing to investigate, but we don't believe our data has been impacted, if you will."
Asked whether the nature of the attack was the latter, where QEC was locked out of its systems and the data encrypted, Nippard said it was still early in the investigation.
"That appears to be the type of cyberattack that we've seen in this case. But it's still very early in the investigation. There's still a lot more details to be investigated."
Whether this was a ransomware attack or not is significant because if it is, this would be the second time in more than three years the Government of Nunavut (GN) has been hit by such a cyberattack.
In November 2019, the GN's entire IT system was hacked. It took six weeks to get all communities restored with core connectivity and applications. QEC was spared, because the public utility isn't part of the GN's IT system.
The 2019 attack cost the department of community and government services alone more than $5.4 million to fix, according to the government's report on the attack. Recovery included replacing more than 1,400 workstations. A synopsis from Microsoft — which was hired by the GN to come in and rebuild the network — notes more than 5,500 devices were affected.
"QEC is not at liberty to discuss the details of the cyberattack," Nippard said when asked outright if this was a ransomware attack, based on the details he had already provided.
"If you can appreciate, this is like untangling a very large knot. It takes time, and it takes some patience. We will get to the bottom of it all, but it's going to take a little bit of time."
Although QEC operates at arm's length of the government's IT infrastructure, the lessons learned from the 2019 attack were shared with the company, Nippard said.
"There will be lessons learned once the investigation is completed this time, that we in turn will share with the GN," he said. "At the same time, that was three years ago, and cybersecurity and cybercriminals, they've all evolved since then. So it's an ongoing battle. A lot has changed in three years."
Email system 'behaved oddly'
Nippard said the attack against QEC was first discovered after an employee tried sending an email to an external recipient but the email system started malfunctioning, as first reported by Nunatsiaq News.
"The email system started behaving rather oddly," Nippard told CBC News, who said the system was rejecting the email trying to be sent.
"It was at that point [the employee] contacted our IT team, and they began an investigation and shut down the network and all of our systems fearing there had been some kind of cyberattack."
Nippard wouldn't elaborate on whether QEC is still locked out as a result of the cyberattack, or QEC's IT team's intervention, although he stressed repeatedly throughout the interview that no customer data had been impacted.
"We aren't going to unlock anything until we're 100 per cent satisfied that there's no risk to QEC and its customers," he said.
"Our power systems continue to work as normal. We're still erring on the side of caution that all customers keep an eye on their financial card data and their credit card statements."


